Okta Customer Identity Cloud (Auth0)
With Okta Customer Identity Cloud (Auth0), your customers can securely log in to the Sana webstore and other applications with their Auth0 accounts using single sign-on (SSO). It provides a simple, secure, and seamless login to the Sana webstore using Auth0 accounts and enforcing all Auth0 security policies.
On May 3, 2021, Okta acquired Auth0.
To allow your webstore customers to log in to the Sana webstore with their Auth0 accounts, you will need to:
- Create a Sana Commerce Cloud application in the Auth0 Dashboard.
- Add users (customers) to the Auth0 Dashboard.
You will also need to connect Sana Commerce Cloud to Auth0, create shop accounts and modify the Login page of your webstore. For more information, see Single Sign-On.
Create an Application
The application is needed to connect Sana Commerce Cloud to Auth0.
Step 1: Sign in to the Auth0 Dashboard.
Step 2: Go to: Applications > Applications.
Step 3: Click Create Application.
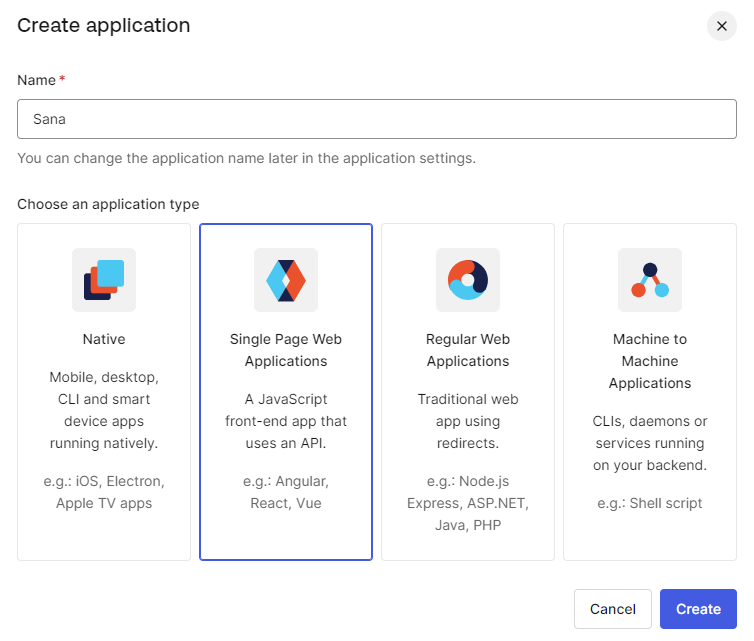
Step 4: On the Create application page, enter a name for your application, for example, Sana Commerce Cloud, Sana, your webstore, or company name.
Step 5: Choose Single Page Web Applications and click Create.
The application is created, and you will see the app details page with various data and settings.
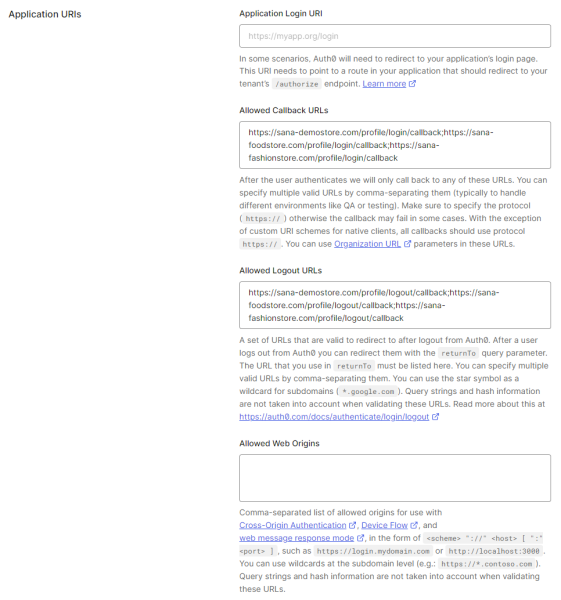
Step 6: On the Settings tab, in the Application URIs section, add Allowed callback URLs and Allowed Logout URLs.
- The allowed callback URL is the URL to which Auth0 redirects users after they authenticate.
- The allowed logout URL is the URL to which Auth0 redirects users after logging out from Auth0.
If you have multiple Sana Commerce Cloud webstores and want to use single sign-on for all your webstores, you must add all your webstore URLs.
- Allowed callback URL format: https://your-webstore-domain.com/profile/login/callback
- Allowed Logout URL format: https://your-webstore-domain.com/profile/logout/callback
If you have a multi-lingual webstore, you need to add all webstore URLs for all languages, for example:
https://your-webstore-domain.com/de-de/profile/login/callback
https://your-webstore-domain.com/de-de/profile/logout/callback
Step 7: Click Save Changes.
When the application is created, you can configure any other settings. For more information about how to create an application and about application settings in Auth0, see Create Applications and Application Settings on the Auth0 website.
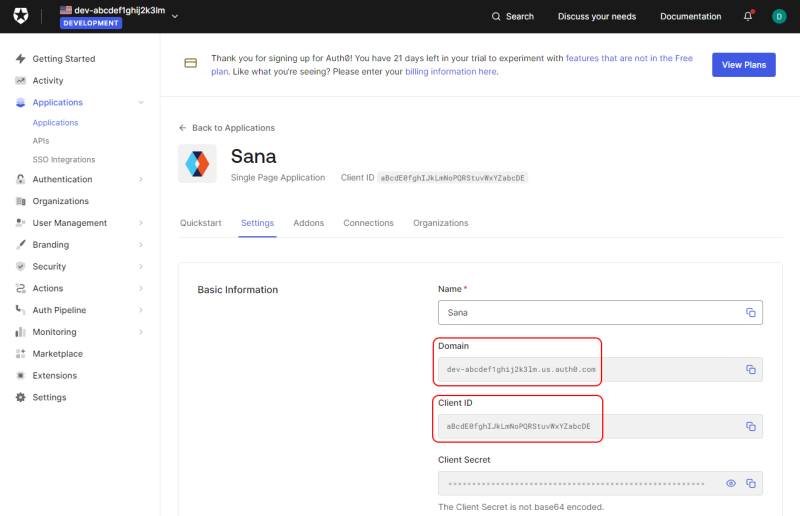
On the Settings tab of your application, in the Basic Information section, see Domain and Client ID. You will need the domain and client ID to connect your Sana Commerce Cloud application to Auth0. Thus, copy these values.
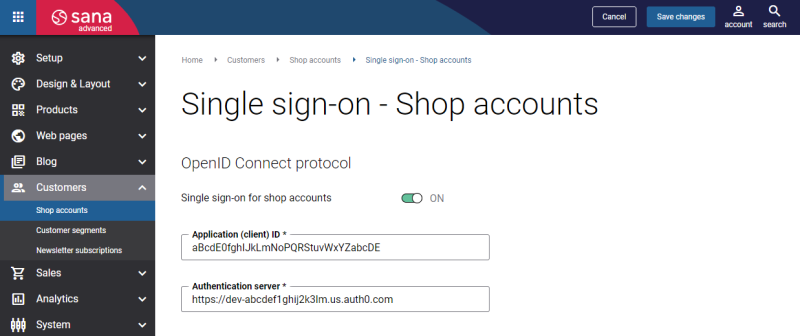
To connect Sana Commerce Cloud to Auth0, you will need to enter your application’s client ID and domain in Sana Admin.
For more information, see Connect Sana Commerce Cloud to Your Identity Provider.
User Accounts
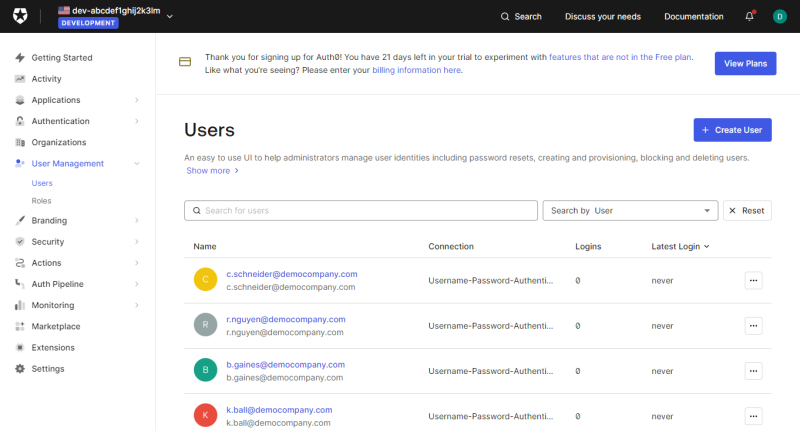
You can create new users in the Auth0 Dashboard or use existing users to allow your webstore customers to log in to the Sana webstore with their Auth0 accounts.
Go to the User Management menu item to create and manage users in the Auth0 Dashboard.
For more information, see Create Users on the Auth0 website.
Users must have access to the application. In Auth0 users are grouped by tenant. All users associated with a single Auth0 tenant are shared between the tenant's applications and therefore have access to the applications.
Using different tenants or rules, you can keep users separate and restrict their access to certain applications.
For more information, see Manage User Access to Applications on the Auth0 website.
Claims for Shop Accounts Creation
Claims are pieces of information about a user that the identity provider sends to the application. They are necessary to automatically create shop accounts in Sana Admin for customers who log in to the Sana webstore with their identity provider accounts.
For more information, see Single Sign-On: Create Shop Accounts in Sana Admin.
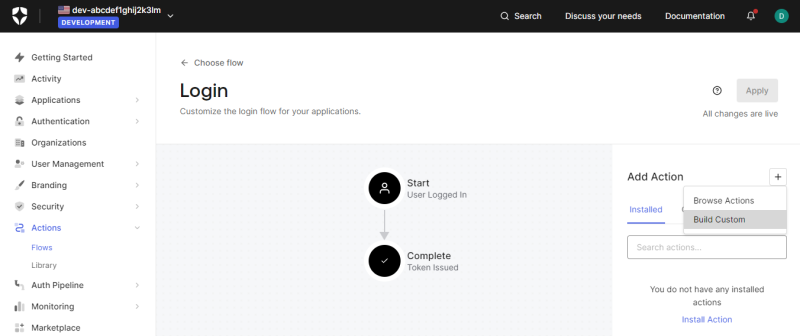
How to Configure Claims
Step 1: Sign in to the Auth0 Dashboard.
Step 2: Go to: Actions > Flows.
Step 3: On the Flows page, click Login.
Step 4: Click Add Action and select Build Custom.
Step 5: Enter the action name and click Create.
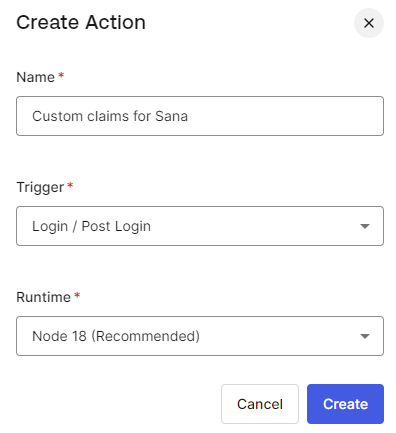
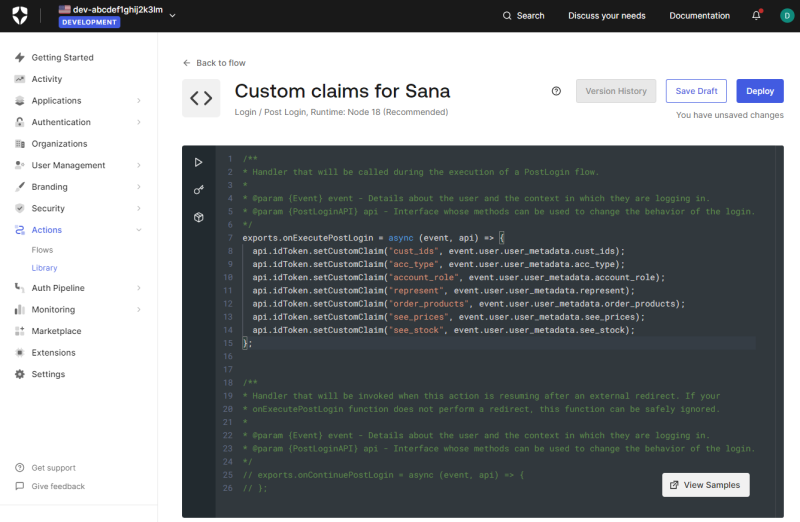
Step 6: Add the necessary claims to the action you created.
You can use any claim name. On the screenshot and in the table below you can see examples of claim names that you can also use. The claim names you specify must also be used to set up claims in Sana Admin.
You can create claims for the following shop account settings:
- Account (customer) ID
- Shop account type
- Account role
- Can order products
- Can see prices
- Can see stock
On the screenshot below you can see all available Sana claims.
api.idToken.setCustomClaim("cust_ids", event.user.user_metadata.cust_ids);
api.idToken.setCustomClaim("acc_type", event.user.user_metadata.acc_type);
api.idToken.setCustomClaim("account_role", event.user.user_metadata.account_role);
api.idToken.setCustomClaim("order_products", event.user.user_metadata.order_products);
api.idToken.setCustomClaim("see_prices", event.user.user_metadata.see_prices);
api.idToken.setCustomClaim("see_stock", event.user.user_metadata.see_stock);Step 7: When the claims have been added, click Deploy.
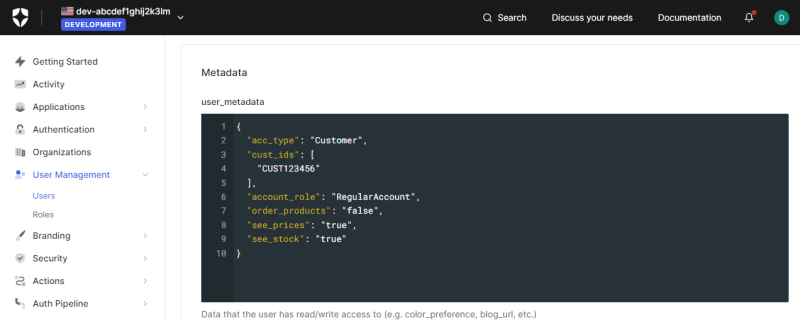
Step 8: Go to: User Management > Users.
Step 9: Click on the user to open the details.
Step 10: On the Details tab, find the Metadata section.
Step 11: Add claims with the necessary values to the user_metadata. This is the user data that will be used to create a shop account for the customer in Sana Admin when this customer logs in to the Sana webstore for the first time with the Auth0 account.
| Shop account settings | Claims | Values |
|---|---|---|
| Account (Customer) ID | cust_ids | Customer ID in ERP
One to Multi relation is supported. See an example of how you can specify multiple customer IDs. Copy |
| Shop account type | acc_type |
|
| Account role | account_role |
|
| Can order products | order_products |
|
| Can see prices | see_prices |
|
| Can see stock | see_stock |
|
Shop Account Roles
Sana Commerce Cloud supports shop account roles when using single sign-on to log in to the Sana webstore with the Auth0 accounts. You can use claims in the Auth0 Dashboard to automatically create shop accounts with the necessary role (regular account, account manager, sub-account) in Sana Admin when customers log in to the Sana webstore for the first time with their Auth0 account.
Examples:
| Regular account | Account manager | Sub-account |
|---|---|---|
|
Copy
|
Copy
|
Copy
|
When a customer logs in to the Sana webstore for the first time with the Auth0 account and the shop account is created, it can be changed in Sana Admin. The claims in the user metadata in the Auth0 Dashboard are only used to create shop accounts.
Limitations
- The account manager cannot change the name and e-mail of sub-accounts logged in to the Sana webstore with their Auth0 accounts. This information is stored in the user details in the Auth0 Dashboard.
- The account manager cannot remove sub-accounts logged in to the Sana webstore with their Auth0 accounts.
Good to Know
If you use a single sign-on for your webstore customers with Auth0:
- You can set up any security policies and restrictions in the Auth0 Dashboard, such as multi-factor authentication (MFA) and others.
- You can block and unblock the user. The blocked users cannot log in to the applications.
- Auth0 controls user password policies, such as password reset. If customers use their Auth0 accounts to log in to the Sana webstore, they cannot use the forgot password functionality of Sana. Instead, they can use Auth0’s functionality, which is managed in the Auth0 Dashboard.