Microsoft Entra ID
With Microsoft Entra ID (formerly known as Azure Active Directory), the Sana Admin users can securely log in to Sana Admin and other applications with their Microsoft accounts using single sign-on (SSO). It provides a simple, secure, and seamless login to Sana Admin using Microsoft accounts and enforcing all Microsoft security policies.

To log in to Sana Admin with a Microsoft account, you will need to:
- Register a Sana Commerce Cloud application in the Microsoft Entra ID.
- Connect Sana Commerce Cloud to Microsoft Entra ID.
- Add a user to Microsoft Entra ID.
- Assign access for a user to the Sana Commerce Cloud application.
- Add a user to Sana Admin to create a connection between a user in Microsoft Entra ID and Sana Admin.
Register a Sana Commerce Cloud Application in the Microsoft Entra ID
The application is needed to connect Sana Commerce Cloud to Microsoft Entra ID.
Step 1: Sign in to the Azure portal.
You must sign in with the Azure account that has an active subscription and permission to manage applications in Microsoft Entra ID.
Step 2: Search for and select Microsoft Entra ID.
Step 3: In the menu on the left, click: App registrations > New registration.
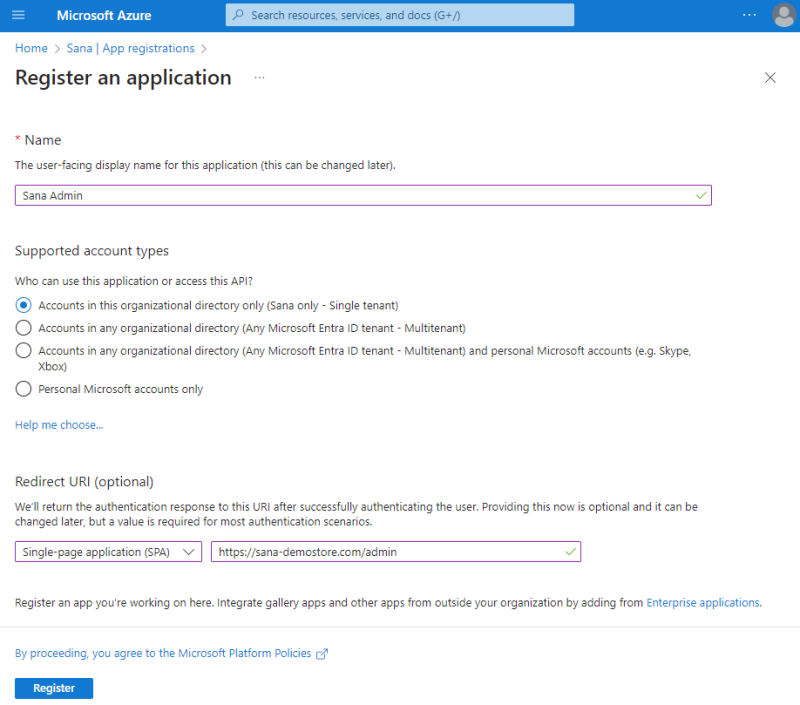
Step 4: Enter a display Name for your application, for example, Sana Commerce Cloud, Sana Admin, or your webstore name.
Step 5: Select the supported account type. You can leave the default value.
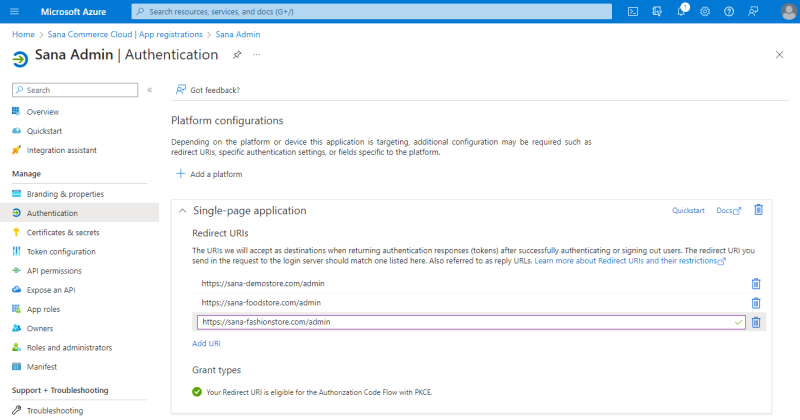
Step 6: In the Redirect URI (optional) section, select the Single-page application (SPA) platform and enter your Sana Admin URL, for example https://yourwebstore.com/admin.
A redirect URI is where the Microsoft identity platform redirects a user's client and sends security tokens after authentication.
If you have multiple Sana Commerce Cloud applications and want to use single sign-on for all your Sana Admin panels, you must add all your Sana Admin URLs to the Redirect URIs section. You can do this on the Authentication page only after the application is registered.
Step 7: Click Register to complete the Sana Commerce Cloud app registration.
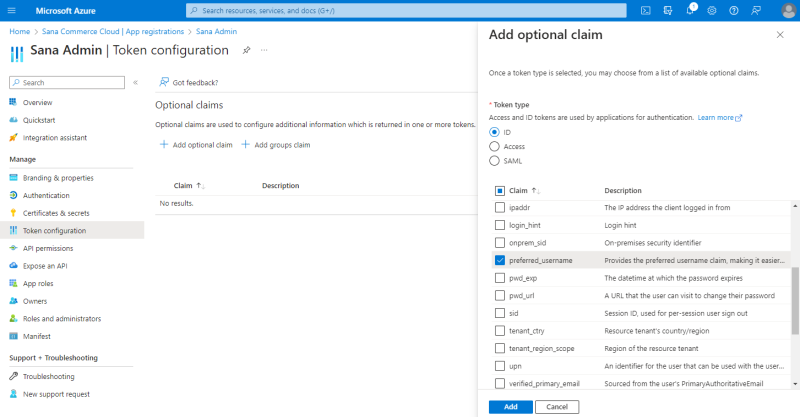
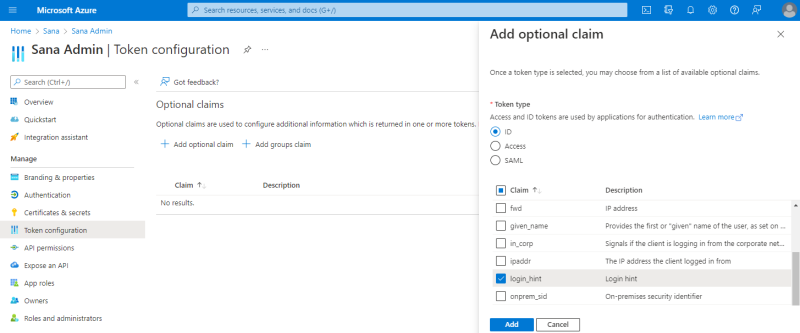
Step 8: When the application is registered, click Token configuration in the menu on the left. Then, click Add optional claim.
Step 9: Select the ID token type. Then, find and select the preferred_username claim, and click Add.
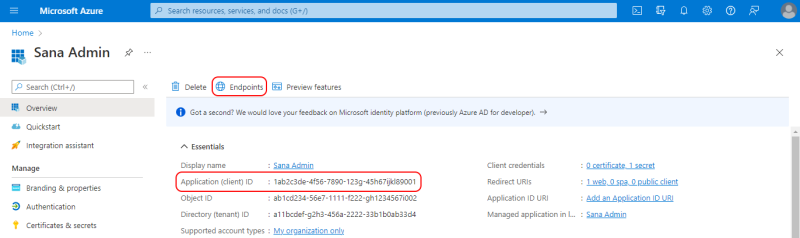
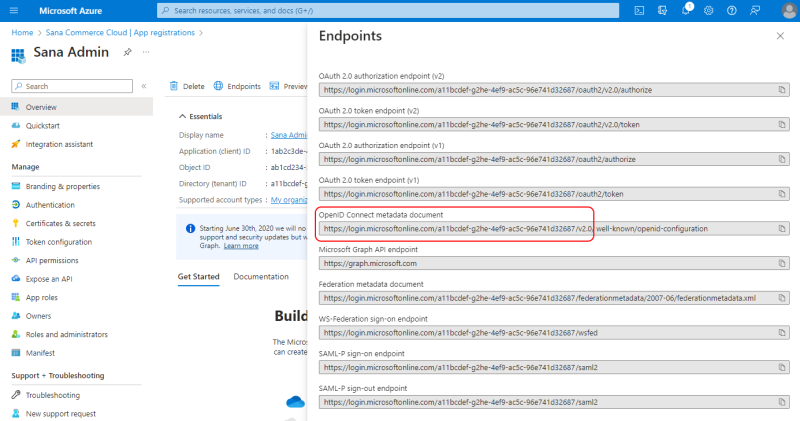
Step 10: Click Overview in the menu on the left to see the details of your application, such as the Application (client) ID. The application (client) ID uniquely identifies your application in the Microsoft identity platform. You will need the application (client) ID to connect your Sana Commerce Cloud application to Microsoft Entra ID. Thus, you can copy it.
You will also need the authentication server. To find it, click Endpoints. See OpenID Connect metadata document. You will need this URL, or rather part of it as shown on the screenshot below.
An example of the URL to enter in Sana Admin as the application server URL:
https://login.microsoftonline.com/a11bcdef-g2he-456f-2222-33b1b0ab33d4/v2.0
For more information, see Quickstart: Register an application with the Microsoft identity platform on the Microsoft website.
Connect Sana Commerce Cloud to Microsoft Entra ID
The single sign-on configuration is global for all your Sana Commerce Cloud applications. This means that if you have multiple webstores, this connection will be used for all your Sana Admin panels. You can only connect Sana Admin to one Microsoft Entra ID.
Step 1: Log in to Sana Admin as a system administrator.
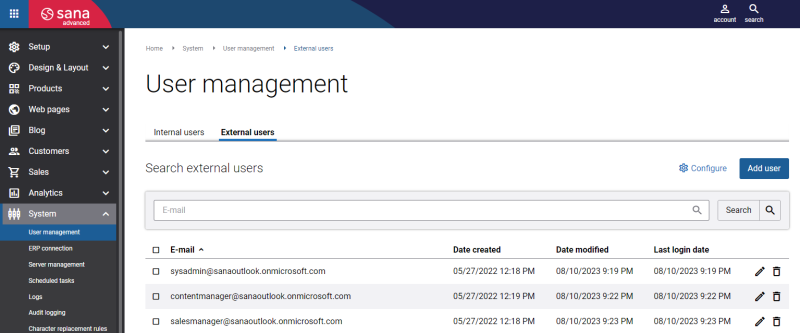
Step 2: Go to: System > User management.
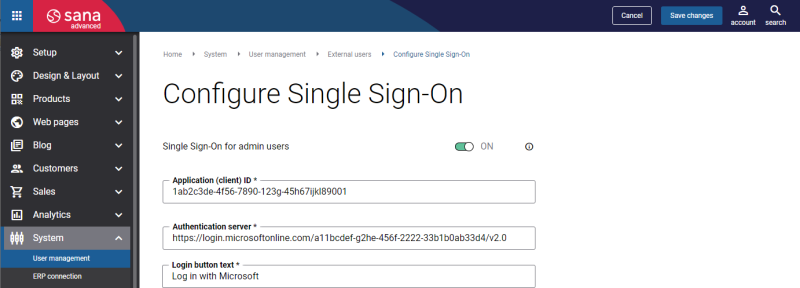
Step 3: Under External users, click Configure.
Step 4: On the Configure Single Sign-On page, enable the option Single Sign-On for admin users, and enter the Application (client) ID and Authentication server of the Sana Commerce Cloud application that you created in the Microsoft Entra ID.
Step 5: Enter the Login button text. It is shown on the Sana Admin login page.
Step 6: Click Save changes.
When Sana Commerce Cloud is connected to Microsoft Entra ID, the login button with the specified text will be shown on the Sana Admin login page.
User Accounts
You can create new users in Microsoft Entra ID or use existing users to log in to Sana Admin with a Microsoft account.
Create a User in Microsoft Entra ID
To add or delete users you must be a User administrator or Global administrator.
Step 1: Sign in to the Azure portal in the User administrator role for the organization.
Step 2: Search for and select Microsoft Entra ID.
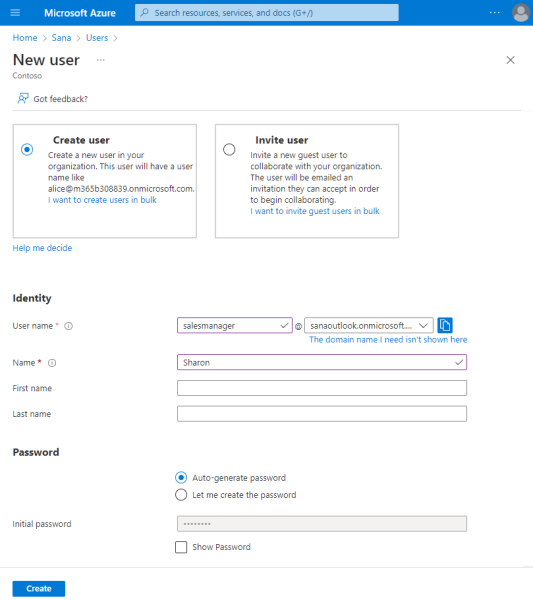
Step 3: Click Users, and then click New user.
Step 4: On the User page, enter information for this user, such as user name and name.
Step 5: Copy the auto-generated or created password provided in the Initial password box. You'll need to give this password to the user to log in to Sana Admin for the first time.
Step 6: Click Create.
The user is created and added to your Microsoft Entra ID organization.
For more information, see Add or delete users on the Microsoft website.
Assign Access for a User to the Sana Commerce Cloud Application in Microsoft Entra ID
You must assign your application in Microsoft Entra ID to users so that they can access it.
Step 1: Sign in to the Azure portal.
Step 2: Search for and select Enterprise applications.
Step 3: Open your Sana Commerce Cloud application.
Step 4: Click Users and groups, and then click Add user/group.
Step 5: On the Add Assignment page, select Users to open the Users selection list.
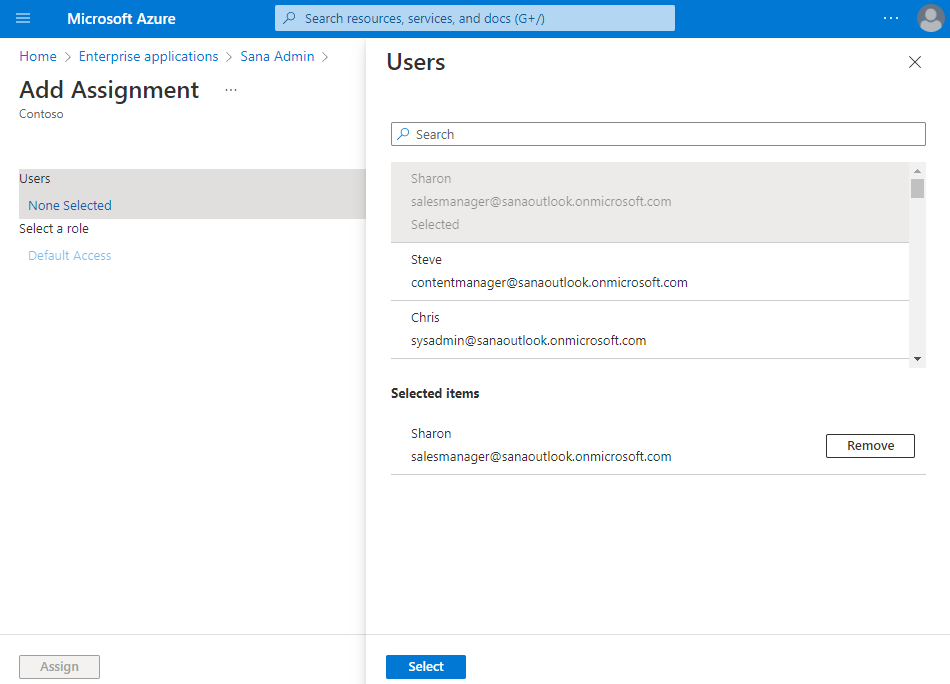
Step 6: Select the necessary users, then click Select to add them to the Add Assignment list.
Step 7: Click Assign to assign the users to the Sana Commerce Cloud application.
For more information, see Using a group to manage access to SaaS applications on the Microsoft website.
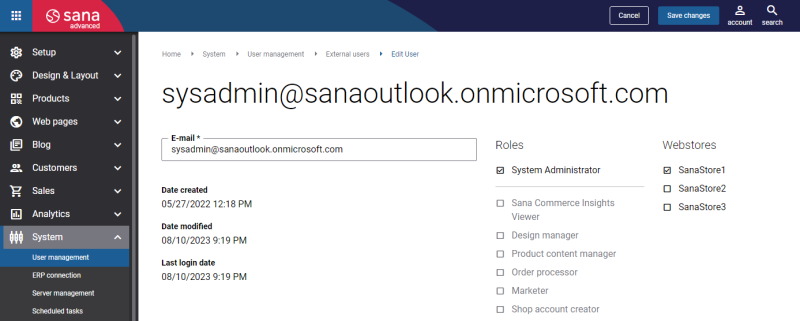
Create a User in Sana Admin
You must link users created in Microsoft Entra ID to the same users in Sana Admin.
Step 1: Log in to Sana Admin as a system administrator.
Step 2: Go to: System > User management.
Step 3: Under External users, click New user.
Step 4: In the E-mail field, enter the e-mail of the user created in the Microsoft Entra ID.
The user's e-mail address must be the same in the Microsoft Entra ID and Sana Admin.
Step 5: Assign one or more roles to the user. The assigned role determines the user's function and permissions within Sana Admin. See the list of permissions for each user role in the Sana Admin User Roles & Permissions file.
Step 6: Select the webstore that the user should have access to. If you have multiple webstores, the user can have access to one or more webstores.
When the Sana Commerce Cloud app is registered in the Microsoft Entra ID, Sana Commerce Cloud is connected to the Microsoft Entra ID, users are created in the Microsoft Entra ID, assigned to the application and connected to the same users in Sana Admin, these users can log in to Sana Admin using their Microsoft accounts.
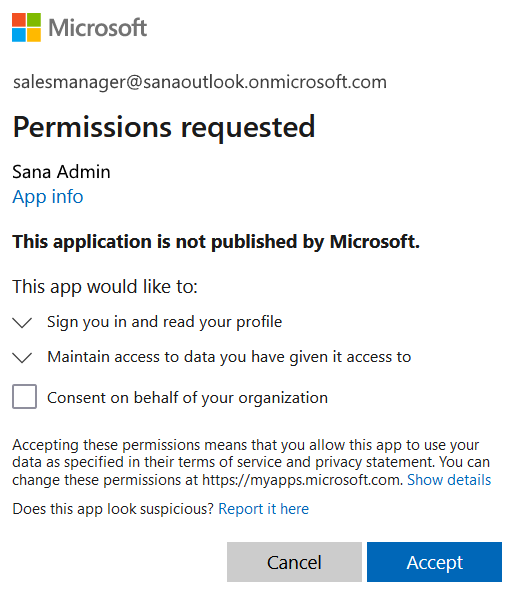
Logging in to Sana Admin for the First Time with a Microsoft Account
If the user logs in to Sana Admin with the Microsoft account for the first time, Microsoft will ask you to accept the permissions required for the Sana Commerce Cloud app created in the Microsoft Entra ID. The user must select the checkbox Consent on behalf of your organization and click Accept.
The user will be asked to agree to the terms and conditions of the end-user license agreement (EULA).
Logging out of Sana Admin
If users have several Microsoft accounts for different purposes and they log out of Sana Admin, users will be asked to choose the account that they want to log out of. The user can choose the necessary Microsoft account and log out of Sana Admin.
If you want to avoid this and log out without choosing the required account, you can add an optional claim to your application. To do this:
Step 1: Go to the Azure portal.
Step 2: Search for and select Microsoft Entra ID.
Step 3: In the menu on the left, click App registrations.
Step 4: Select the Sana Commerce Cloud application you want to configure optional claims for in the list.
Step 5: Go to Token configuration and click Add optional claim.
Step 6: Select the ID token type. Then, find and select the login_hint claim, and click Add.
If you add the login_hint claim to the Sana Commerce Cloud app, the user will not need to choose the Microsoft account to log out of Sana Admin.
For more information, see Configure optional claims on the Microsoft website.
Good to Know
If you use a single sign-on for your Sana Admin users with Microsoft Entra ID:
- You can set up any security policies and restrictions in Microsoft Entra ID, such as multi-factor authentication (MFA) and others.
- You can enable and disable the account in Microsoft Entra ID. The disabled users cannot log in to the applications.
- Microsoft Entra ID controls user password policies, such as password reset and password expiration. If users use their Microsoft accounts to log in to Sana Admin, they cannot use the forgot password functionality of Sana. Instead, they can use Microsoft's functionality, which is managed in the Azure portal.