Azure Active Directory B2C
Effective May 1, 2025, Microsoft will no longer sell Azure AD B2C to new customers, but existing Azure AD B2C customers can continue using the product. Microsoft will continue to support Azure AD B2C until at least May 2030. Microsoft has launched its next-generation product, Entra External ID. For more details, refer to the Azure AD B2C FAQ.
With Microsoft Azure Active Directory B2C, your customers can securely log in to the Sana webstore and other applications with their identity provider accounts using single sign-on (SSO). It supplies a simple, secure, and seamless login to the Sana webstore using identity provider accounts and enforcing all security policies.
To allow your webstore customers to log in to the Sana webstore with their identity provider accounts, you will need to:
- Create an Azure Active Directory B2C (Azure AD B2C) tenant
- Register a Sana Commerce Cloud application in Azure Active Directory B2C
- Create a sign-in user flow
- Manage user accounts
You will also need to connect Sana Commerce Cloud to Azure Active Directory B2C, create shop accounts, and modify the Login page of your webstore. For more information, see Single Sign-On.
Prerequisites
- An Azure account with an active subscription.
- An Azure Active Directory B2C tenant linked to your Azure subscription. If you have multiple tenants, switch to the necessary one.
Create an Azure Active Directory B2C Tenant
All applications interacting with Azure Active Directory B2C must be registered in a B2C tenant. You can use an existing tenant or create a new one.
For more information on creating a tenant, see Create an Azure Active Directory B2C tenant on the Microsoft website.
Register a Sana Commerce Cloud Application in Azure Active Directory B2C
The application is needed to connect Sana Commerce Cloud to Azure Active Directory B2C.
Step 1: Sign in to the Azure portal.
Step 2: In the Azure portal, search for and select Azure AD B2C.
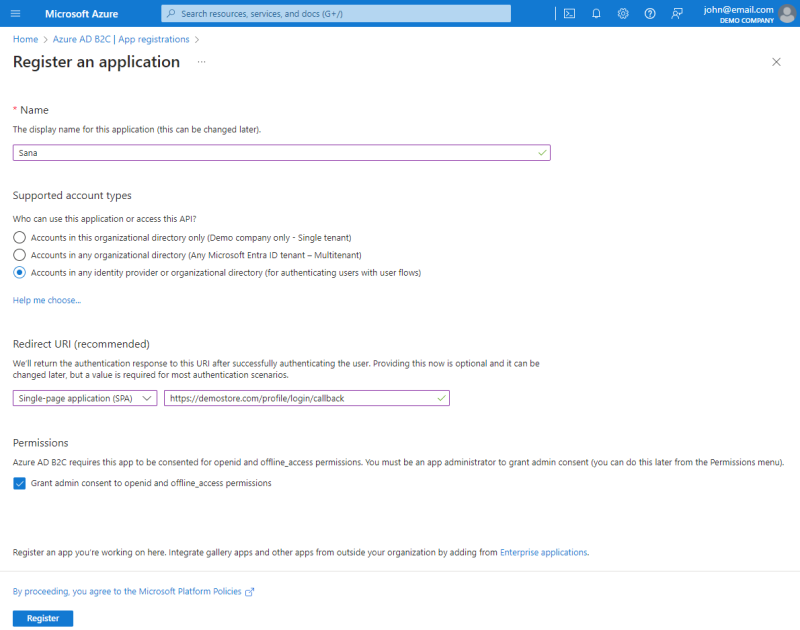
Step 3: In the menu on the left, click: App registrations > New registration.
Step 4: Enter a Name for your application, for example, Sana Commerce Cloud, Sana, your webstore, or company name.
Step 5: Under Supported account types, select Accounts in any identity provider or organizational directory (for authenticating users with user flows).
Step 6: Under Redirect URI, select Single-page application (SPA), and enter your webstore URL in the following format: https://your-webstore-domain.com/profile/login/callback.
A redirect URI is where the Microsoft identity platform redirects a user's client and sends security tokens after authentication.
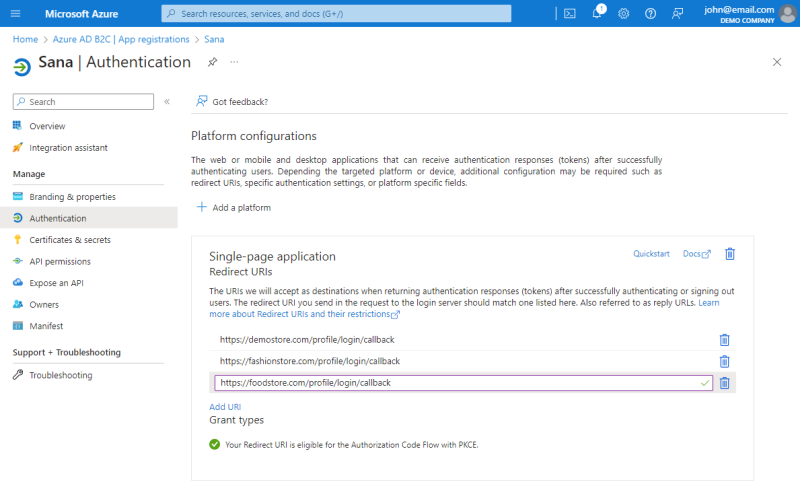
If you have multiple Sana Commerce Cloud webstores and want to use single sign-on for all your webstores, you must add all your webstore URLs to the Redirect URIs section. You can do this on the Authentication page only after the application is registered.
If you have a multi-lingual webstore, you need to add all webstore URLs for all languages, for example:
https://your-webstore-domain.com/de-de/profile/login/callback
Step 7: Under Permissions, select the checkbox Grant admin consent to openid and offline_access permissions.
Step 8: Click Register.
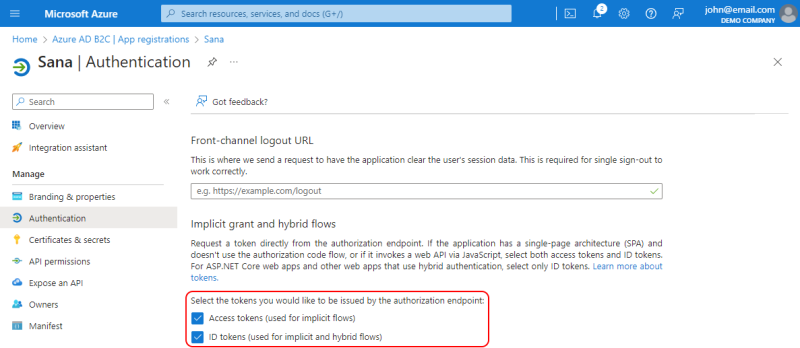
Step 9: When the application is created, on the Authentication page, select Access tokens and ID tokens for your application.
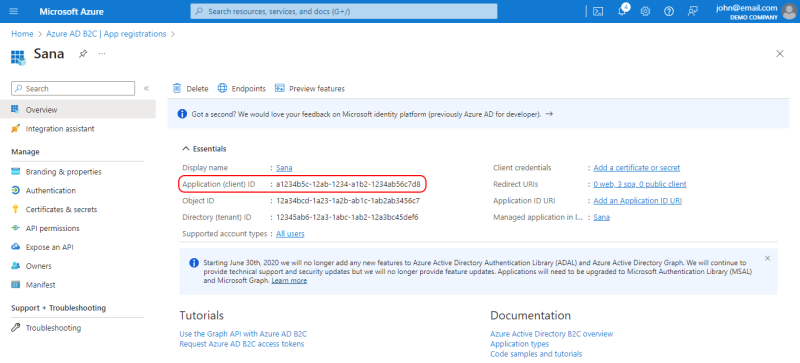
Step 10: On the Overview page of the created application, copy the Application (client) ID.
The Application (client) ID is used in Sana Admin to connect to Azure Active Directory B2C. Copy it to Single sign-on - Shop accounts configuration in Sana Admin or somewhere else to configure it later. In Sana Admin, you need to enter it twice on the Single sign-on - Shop accounts page: in the Application (client) ID field and in the Custom scopes field.
For more information, see Register a single-page application in Azure Active Directory B2C on the Microsoft website.
Create a Sign-in User Flow
User flows in Azure Active Directory B2C (Azure AD B2C) define the logic users must follow to access your application. You need to create a sign-in user flow to allow customers to log in to the Sana webstore.
Step 1: Sign in to the Azure portal.
Step 2: In the Azure portal, search for and select Azure AD B2C.
Step 3: Under Policies, click User flows, and then New user flow.
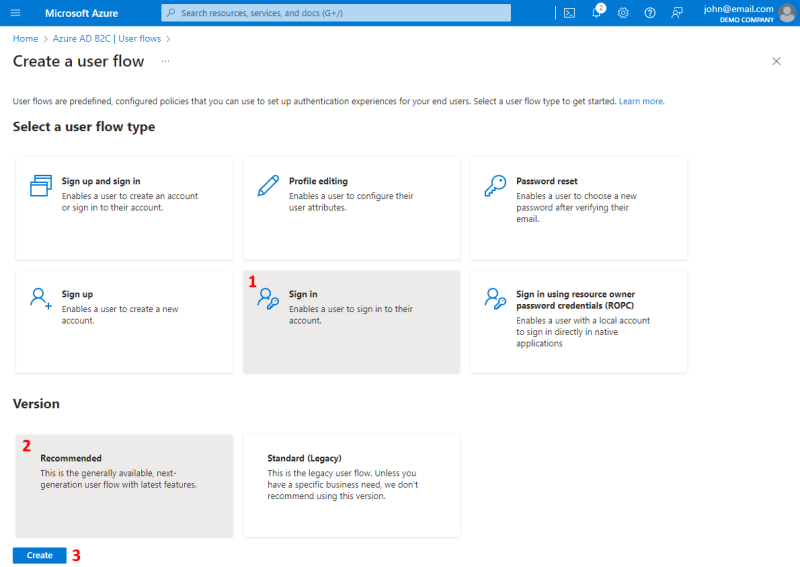
Step 4: On the Create a user flow page, select the Sign in user flow and the Recommended version.
Step 5: Click Create to create a user flow.
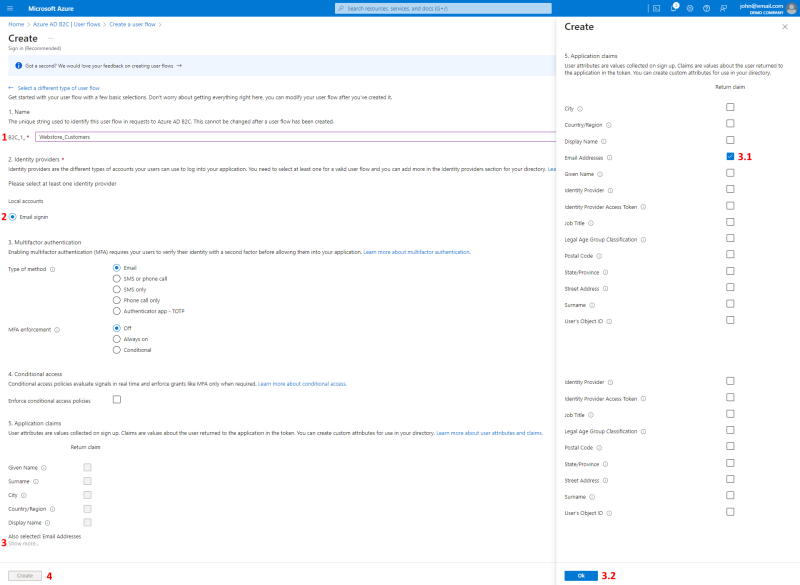
Step 6: Enter a Name for the user flow.
Step 7: Under Local accounts, select Email signin.
Step 8: Under Application claims, select Email Addresses.
For the full list of application claims, click Show more, select the Email Addresses claim, and then click Ok.
Step 9: Click Create to add the user flow.
For more information, see Create user flows and custom policies in Azure Active Directory B2C and Set up a sign-up and sign-in flow in Azure Active Directory B2C on the Microsoft website.
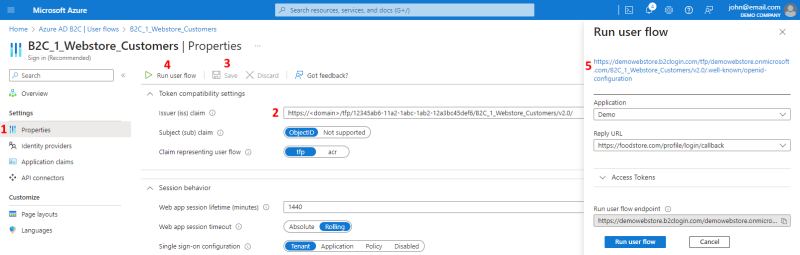
Step 10: Open the user flow Properties and under Token compatibility settings, select the Issuer (iss) claim with the user flow you have created.
Step 11: Click Save to save changes to the user flow.
Step 12: Click Run user flow. Click on the link at the top of the Run user flow window.
Step 13: Clicking on the link will open the page where you must copy the link specified for the issuer.
It should be in the following format: https://<domain>/tfp/<tenant-id>/<userflow>/v2.0.
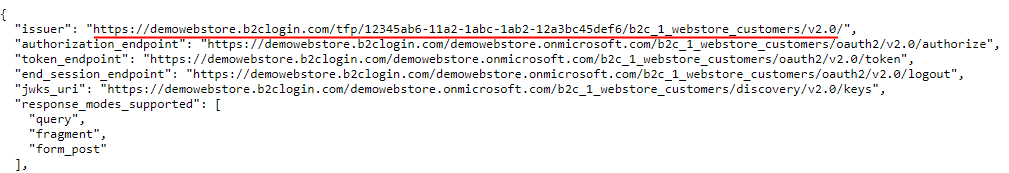
Sana Commerce Cloud also supports the following link format for Microsoft Azure Active Directory B2C: https://<tenant-id>.ciamlogin.com/<tenant-id>/v2.0/.
This link is used for the Application server in Sana Admin to connect to Azure Active Directory B2C. Copy this link to Single sign-on - Shop accounts configuration in Sana Admin or somewhere else to configure it later.
User Accounts
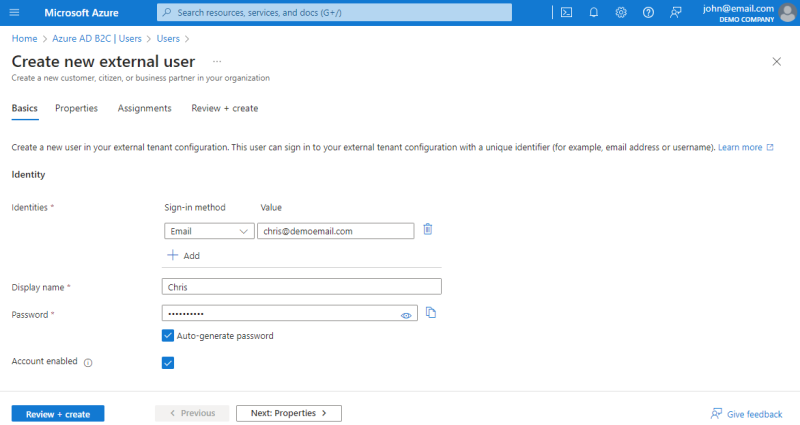
You can create new users in the Azure portal or use existing users to allow your webstore customers to log in to the Sana webstore with their Azure AD B2C accounts.
If Azure AD B2C accounts are used to log in to the webstore, shop accounts must also be created in Sana Admin. Only customers with shop accounts can log in to the webstore. For more information, see Single Sign-On.
To ensure seamless access, all accounts must use the email sign-in method. This means that only users who have email can be used. This is necessary because the user's email address must align across both Azure AD B2C and Sana Admin. Only when the user's email address matches in both, the Sana Admin shop accounts and Azure AD B2C accounts, customer can successfully log in to the Sana webstore.
In Azure AD B2C, users can have multiple email addresses. Sana Commerce Cloud can only use the first email address for user authentication.
For more information, see Sign-in options in Azure AD B2C on the Microsoft website.
Claims for Shop Accounts Creation
Claims are pieces of information about a user that the identity provider sends to the application. They are necessary to automatically create shop accounts in Sana Admin for customers who log in to the Sana webstore with their identity provider accounts.
For more information, see Single Sign-On: Create Shop Accounts in Sana Admin.
To configure custom claims (attributes) in Azure Active Directory B2C:
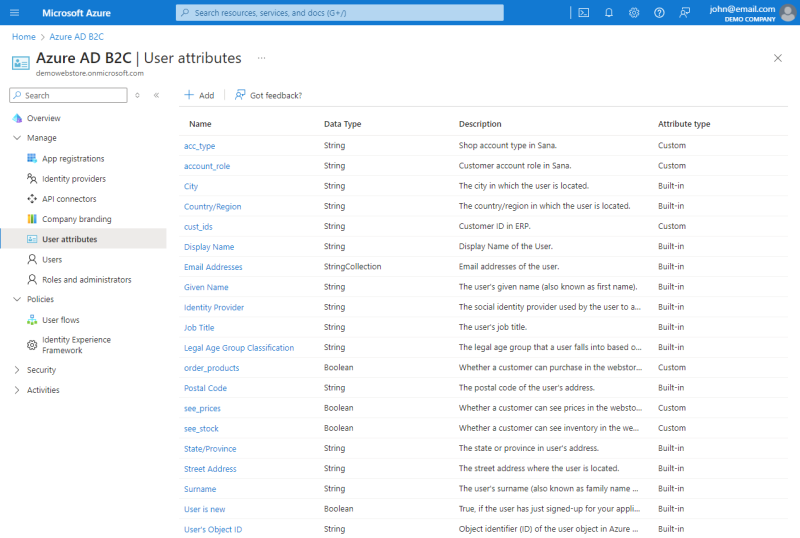
Step 1: Create user attributes in Azure AD B2C and use them in your user flow. For detailed instructions on how to do this, please refer to the official Microsoft documentation: Define custom attributes in Azure Active Directory B2C.
You can create the following user attributes and use them in your user flow.
| Attribute name | Data type |
|---|---|
| cust_ids | String |
| account_role | String |
| acc_type | String |
| see_prices | Boolean |
| see_stock | Boolean |
| order_products | Boolean |
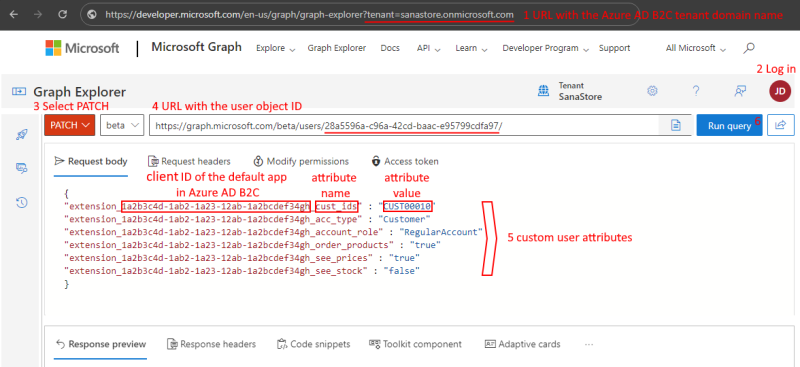
Step 2: Log in to the Microsoft Graph Explorer to set the custom attribute values for the shop accounts.
You must use your Azure AD B2C tenant domain name in the Microsoft Graph Explorer URL.
URL format: https://developer.microsoft.com/en-us/graph/graph-explorer?tenant={your-tenant-domain}
Example: https://developer.microsoft.com/en-us/graph/graph-explorer?tenant=sanastore.onmicrosoft.com
Step 3: To set the custom attribute values for the shop accounts:
3.1 Select PATCH.
3.2 Enter the following URL with the object ID of the user.
URL format: https://graph.microsoft.com/beta/users/{object-id-of-the-user}/
Example: https://graph.microsoft.com/beta/users/28a5596a-c96a-42cd-baac-e95799cdfa97/
3.3 In the Request body, specify the attributes you want to add to the user. See the example in the screenshot below. The highlighted parts must be replaced.
Format: "extension_{AzureADB2C-DefaultApp-ClientID}_{attribute_name}" : "attribute_value"
Example:
{
"extension_1a2b3c4d-1ab2-1a23-12ab-1a2bcdef34gh_cust_ids" : "CUST00010",
"extension_1a2b3c4d-1ab2-1a23-12ab-1a2bcdef34gh_acc_type" : "Customer",
"extension_1a2b3c4d-1ab2-1a23-12ab-1a2bcdef34gh_account_role" : "RegularAccount",
"extension_1a2b3c4d-1ab2-1a23-12ab-1a2bcdef34gh_order_products" : "true",
"extension_1a2b3c4d-1ab2-1a23-12ab-1a2bcdef34gh_see_prices" : "true",
"extension_1a2b3c4d-1ab2-1a23-12ab-1a2bcdef34gh_see_stock" : "false"
}| Shop account settings | Attribute names | Attribute values |
|---|---|---|
| Account (customer) ID | cust_ids | Customer ID in ERP |
| Shop account type | account_role |
|
| Account role | acc_type |
|
| Can order products | see_prices |
|
| Can see prices | see_stock |
|
| Can see stock | order_products |
|
3.4 Click Run query.
When the query is executed, custom attributes should be added to the user. The user should be able to log in to the Sana webstore, and the shop account should be automatically created in Sana Admin with the specified attribute values.
Limitations
-
Session revoking is not supported.
-
One to multi account relation: To support one to multi relation, Sana Commerce Cloud expects string collection in the customer ID token claim.
Example: "cust_ids": [ "CUSTOMER-1", "CUSTOMER-2", "CUSTOMER-3" ]
By default, Azure AD B2C does not support arrays, which means achieving one to multi relation support requires implementing custom policies. For more information, see Tutorial: Create user flows and custom policies in Azure Active Directory B2C on the Microsoft website.
Good to Know
If you use a single sign-on for your webstore customers with Azure Active Directory B2C:
- You can set up any security policies and restrictions in Azure Active Directory B2C, such as multi-factor authentication (MFA) and others.
- You can enable and disable the account in Azure Active Directory B2C. The disabled users cannot log in to the applications.
- Azure Active Directory B2C controls user password policies, such as password reset and password expiration. If customers use their Azure AD B2C accounts to log in to the Sana webstore, they cannot use the forgot password functionality of Sana. Instead, they can use Microsoft's functionality, which is managed in the Azure portal.